| Q 1: | All changes made by a transaction are made permanent in the database only after transaction :- | |||||||||
| (1) | FINAL | |||||||||
| (2) | ROLL BACK | |||||||||
| (3) | ABORT | |||||||||
| (4) | COMMIT | |||||||||
| Correct Answer: COMMIT | ||||||||||
| Q 2: | The problem that occur when one transaction update a database item and then the transaction failed for some reason is.................. | |||||||||
| (1) | Temporary select problem | |||||||||
| (2) | Temporary modify problem | |||||||||
| (3) | Dirty read problem | |||||||||
| (4) | None of these | |||||||||
| Correct Answer: None of these | ||||||||||
| Q 3: | In which normal form decomposition of a relationship is lossless join but may not be dependency preserving. | |||||||||
| (1) | PJNF | |||||||||
| (2) | BCNF | |||||||||
| (3) | 3NF | |||||||||
| (4) | All of these | |||||||||
| Correct Answer: BCNF | ||||||||||
| Q 4: | That transactional concurrency leads to increase | |||||||||
| (1) | Integrity | |||||||||
| (2) | Consistency | |||||||||
| (3) | Mutual execution | |||||||||
| (4) | Throughput | |||||||||
| Correct Answer: Throughput | ||||||||||
| Q 5: | In a relational algebra, the Cartesian product is | |||||||||
| (1) | Unity operator | |||||||||
| (2) | Binary operator | |||||||||
| (3) | Ternary operator | |||||||||
| (4) | None of these | |||||||||
| Correct Answer: Binary operator | ||||||||||
| Q 6: | The DROPTABLE statement: | |||||||||
| (1) | Deletes the table structure only | |||||||||
| (2) | Deletes the table structure along with the table data | |||||||||
| (3) | Work weather or not referential integrity constraints would be violated | |||||||||
| (4) | Is not a SQL statement | |||||||||
| Correct Answer: Deletes the table structure along with the table data | ||||||||||
| Q 7: | "Employee's salary should not be greater than rupees 7000". This is an example of | |||||||||
| (1) | Infeasible constraint | |||||||||
| (2) | Overdefined constraint | |||||||||
| (3) | Integrity constraint | |||||||||
| (4) | Field constraint | |||||||||
| Correct Answer: Overdefined constraint | ||||||||||
| Q 8: | E-R diagram, the term cardinality is a synonyms of the term | |||||||||
| (1) | Attribute | |||||||||
| (2) | Degree | |||||||||
| (3) | Entities | |||||||||
| (4) | Cartesian | |||||||||
| Correct Answer: Degree | ||||||||||
| Q 9: | Which one of the following techniques is sometimes used to solve integrity problems in a concurrent transaction scenario? | |||||||||
| (1) | First - come first - served | |||||||||
| (2) | Greedy algorithms | |||||||||
| (3) | Strassens's algorithm | |||||||||
| (4) | Two-phase locking | |||||||||
| Correct Answer: Two-phase locking | ||||||||||
| Q 10: | When the referential integrity rule is enforced, which one is usually not a valid action in response to the deletion of a row that contains a primary key value referenced elsewhere? | |||||||||
| (1) | Do not allow the deletion | |||||||||
| (2) | Accept the deletion without any other action | |||||||||
| (3) | Delete this related rows | |||||||||
| (4) | Set the foreign keys of related rows to mull | |||||||||
| Correct Answer: Accept the deletion without any other action | ||||||||||
| Q 11: | Which of the following it's turn off the data manipulation language (DML) ? | |||||||||
| (1) | It is used to define the physical characteristics of each record | |||||||||
| (2) | It cannot interface with high level programming language | |||||||||
| (3) | It refers to data using physical addresses | |||||||||
| (4) | None of these | |||||||||
| Correct Answer: None of these | ||||||||||
| Q 12: | Which of the following is an assertion in DBMS? | |||||||||
| (1) | Domain constraint | |||||||||
| (2) | View | |||||||||
| (3) | Generalization | |||||||||
| (4) | Trigger | |||||||||
| Correct Answer: Domain constraint | ||||||||||
| Q 13: | Which advantages does a Distributed database has over a centralized database? | |||||||||
| (1) | Slow Response | |||||||||
| (2) | Overall complexity | |||||||||
| (3) | Modular growth | |||||||||
| (4) | Software Cost | |||||||||
| Correct Answer: Modular growth | ||||||||||
| Q 14: | GRANT and REVOKE are - | |||||||||
| (1) | Mandatory Access Control | |||||||||
| (2) | Discretionary Access Control | |||||||||
| (3) | Database Access Control | |||||||||
| (4) | DBMS Access Control | |||||||||
| Correct Answer: Discretionary Access Control | ||||||||||
| Q 15: | Recovery in a distributed DBMS is achieved using? | |||||||||
| (1) | Commit Protocol | |||||||||
| (2) | Revoke Protocol | |||||||||
| (3) | Un-Commit Protocol | |||||||||
| (4) | None of the above | |||||||||
| Correct Answer: Commit Protocol | ||||||||||
| Q 16: | Which SQL statement below is equivalent to: SELECT NAME FROM EMPLOYEE WHERE HOMETOWN='KA'; | |||||||||
| (1) | SELECT NAME IN EMPLOYEE WHERE HOMETOWN IN ('KA'); | |||||||||
| (2) | SELECT NAME IN EMPLOYEE WHERE HOMETOWN = 'KA'; | |||||||||
| (3) | SELECT NAME IN EMPLOYEE WHERE HOMETOWN = 'K'; | |||||||||
| (4) | SELECT NAME FROM EMPLOYEE WHERE HOMETOWN IN ('KA') | |||||||||
| Correct Answer: SELECT NAME FROM EMPLOYEE WHERE HOMETOWN IN ('KA') | ||||||||||
| Q 17: | Architecture of the database can be viewed as | |||||||||
| (1) | two levels. | |||||||||
| (2) | four levels. | |||||||||
| (3) | three levels. | |||||||||
| (4) | one levels. | |||||||||
| Correct Answer: three levels. | ||||||||||
| Q 18: | Fourth normal form (4 NF) relations are needed when | |||||||||
| (1) | there are multivalued dependencies between attributes in composite key | |||||||||
| (2) | there are more then one composite key | |||||||||
| (3) | there are two or more overlapping composite keys | |||||||||
| (4) | there are multivalued dependency between non-key attributes | |||||||||
| Correct Answer: there are multivalued dependencies between attributes in composite key | ||||||||||
| Q 19: | Transaction timestamp is | |||||||||
| (1) | Not unique for each transaction | |||||||||
| (2) | Larger for older transaction | |||||||||
| (3) | Unique identifier assigned for each transaction | |||||||||
| (4) | None of the above | |||||||||
| Correct Answer: Unique identifier assigned for each transaction | ||||||||||
| Q 20: | Which of the following is the process of selecting the data storage and data access characteristics of the database? | |||||||||
| (1) | Logical database design | |||||||||
| (2) | Physical database design | |||||||||
| (3) | Testing and performance tuning | |||||||||
| (4) | Evaluation and selecting | |||||||||
| Correct Answer: Physical database design | ||||||||||
| Q 21: | Which of the following technique is an alternative to log based recovery? | |||||||||
| (1) | Shadow paging | |||||||||
| (2) | Locks | |||||||||
| (3) | Check points | |||||||||
| (4) | Recovery with current transactions | |||||||||
| Correct Answer: Shadow paging | ||||||||||
| Q 22: | The most widely used conceptual model is the ___________. | |||||||||
| (1) | E-R model | |||||||||
| (2) | Chen model | |||||||||
| (3) | External model | |||||||||
| (4) | Attribute model | |||||||||
| Correct Answer: E-R model | ||||||||||
| Q 23: | Which of the following is correct? | |||||||||
| (1) | Function dependencies are not associated with relations; they are based on the semantics of information that we are dealing with | |||||||||
| (2) | If a relation has no redundant information its attributes must not have any function dependencies | |||||||||
| (3) | the FDs that hold for attributes of a relation need not be satisfied at all times | |||||||||
| (4) | BCNF is a fourth normal form. | |||||||||
| Correct Answer: Function dependencies are not associated with relations; they are based on the semantics of information that we are dealing with | ||||||||||
| Q 24: | Horizontal Fragmentation is | |||||||||
| (1) | Divide the data up by logical groups of records | |||||||||
| (2) | Divide the data up by logical groups of attributes | |||||||||
| (3) | Divide the data up by logical groups of entities | |||||||||
| (4) | Divide the data up by logical groups of files | |||||||||
| Correct Answer: Divide the data up by logical groups of records | ||||||||||
| Q 25: | What is the result of the following query? SELECT FLOOR(3.6) FROM DUAL? | |||||||||
| (1) | 3.5 | |||||||||
| (2) | 3.0 | |||||||||
| (3) | 4.0 | |||||||||
| (4) | 3.7 | |||||||||
| Correct Answer: 3.7 | ||||||||||
| Q 26: | The goal of ________ is the protection of data from accidental or international threats to its integrity and access. | |||||||||
| (1) | Rollback | |||||||||
| (2) | Integrity | |||||||||
| (3) | Save point | |||||||||
| (4) | Commit | |||||||||
| Correct Answer: Commit | ||||||||||
| Q 27: | What are "Raw" facts such as telephone number, birth date, sales value etc are called? | |||||||||
| (1) | Record | |||||||||
| (2) | Data | |||||||||
| (3) | File | |||||||||
| (4) | Field | |||||||||
| Correct Answer: Data | ||||||||||
| Q 28: | Which of the following are introduced to reduce the overheads caused by the log-based recovery? | |||||||||
| (1) | Checkpoints | |||||||||
| (2) | Indices | |||||||||
| (3) | Deadlocks | |||||||||
| (4) | Locks | |||||||||
| Correct Answer: Checkpoints | ||||||||||
| Q 29: | An alternative is to organize the sequential file physically is a- | |||||||||
| (1) | Linked List | |||||||||
| (2) | List | |||||||||
| (3) | Stack | |||||||||
| (4) | Queue | |||||||||
| Correct Answer: Linked List | ||||||||||
| Q 30: | In a DBMS, you can - | |||||||||
| (1) | Create a file | |||||||||
| (2) | Delete a file | |||||||||
| (3) | Retrieve a file | |||||||||
| (4) | All of the above | |||||||||
| Correct Answer: All of the above | ||||||||||
| Q 31: | This set of related data item is called- | |||||||||
| (1) | table | |||||||||
| (2) | file | |||||||||
| (3) | record | |||||||||
| (4) | None of the above | |||||||||
| Correct Answer: record | ||||||||||
| Q 32: | ______ is used to develop back-end of an application. | |||||||||
| (1) | GUI | |||||||||
| (2) | Statement | |||||||||
| (3) | Database | |||||||||
| (4) | Form | |||||||||
| Correct Answer: Database | ||||||||||
| Q 33: | SELECT is a- | |||||||||
| (1) | DCL Statement | |||||||||
| (2) | DDL Statement | |||||||||
| (3) | DML Statement | |||||||||
| (4) | TCL Statement | |||||||||
| Correct Answer: DML Statement | ||||||||||
| Q 34: | Which of the following is a valid SQL type? | |||||||||
| (1) | FLOAT | |||||||||
| (2) | NUMERIC | |||||||||
| (3) | CHARACTER | |||||||||
| (4) | All of the above | |||||||||
| Correct Answer: All of the above | ||||||||||
| Q 35: | The ________ database is the most widely used database structure. | |||||||||
| (1) | General | |||||||||
| (2) | Hierarchical | |||||||||
| (3) | Standard | |||||||||
| (4) | Relational | |||||||||
| Correct Answer: Relational | ||||||||||
| Q 36: | A relational Database Management System (RDBMS) package manager data is more than one file at once. How does it organize these files? | |||||||||
| (1) | Table | |||||||||
| (2) | Relation | |||||||||
| (3) | Tuple | |||||||||
| (4) | Both (a) and (b) | |||||||||
| Correct Answer: Both (a) and (b) | ||||||||||
| Q 37: | Let R=(A,B,C,D,E,F) be a relation scheme with the following dependencies : C->F, E->A, EC->D, A->B. Which of the following is a key for R? | |||||||||
| (1) | CD | |||||||||
| (2) | EC | |||||||||
| (3) | AE | |||||||||
| (4) | AC | |||||||||
| Correct Answer: EC | ||||||||||
| Q 38: | Generally speaking, for a weak entity set to be meaningul it must be part of a | |||||||||
| (1) | One-to-one relationship | |||||||||
| (2) | one-to-many relationship | |||||||||
| (3) | Many-to-many relationship | |||||||||
| (4) | None of the above | |||||||||
| Correct Answer: one-to-many relationship | ||||||||||
| Q 39: | Select the correct statement from the following on referential integrity. | |||||||||
| (1) | Referential integrity constraints check whether the primary key values are unique. | |||||||||
| (2) | Referential integrity constraints are specified between two relation in a schema. | |||||||||
| (3) | Referential integrity constraints check whether an attribute value lies in the given range. | |||||||||
| (4) | Referential integrity constraints are specified between entities having recursive relationship. | |||||||||
| Correct Answer: Referential integrity constraints are specified between two relation in a schema. | ||||||||||
| Q 40: | Consider the relation R with four attributes A,B,C and D the functional dependencies {(A,B)→(C,D) and C → D} Which of the following statements is/are correct? | |||||||||
| (1) | C is key for relation R | |||||||||
| (2) | R is in 3 NF | |||||||||
| (3) | Functional dependency C → D violates 3 NF | |||||||||
| (4) | R is in BCNF | |||||||||
| Correct Answer: Functional dependency C → D violates 3 NF | ||||||||||
| Q 41: | Which of the following relational algebraic operation is not a commutative operation? | |||||||||
| (1) | Union | |||||||||
| (2) | Intersection | |||||||||
| (3) | Selection | |||||||||
| (4) | Projection | |||||||||
| Correct Answer: Projection | ||||||||||
| Q 42: | Which of the following is correct? | |||||||||
| (1) | An SQL query automatically eliminates duplicates. | |||||||||
| (2) | An SQL query will not work if there are no indexes on the relations. | |||||||||
| (3) | SQL permits attribute names to be repeated in the same relation. | |||||||||
| (4) | None of the above | |||||||||
| Correct Answer: None of the above | ||||||||||
| Q 43: | Which of the following schemes are used for ensuring atomicity? | |||||||||
| (1) | Log with immediate modification | |||||||||
| (2) | Log with deferred modification | |||||||||
| (3) | Shadow Paging | |||||||||
| (4) | All of the above | |||||||||
| Correct Answer: All of the above | ||||||||||
| Q 44: | Which of the following is true for two-phase locking? | |||||||||
| (1) | Lock acquisition is the second phase | |||||||||
| (2) | Lock can be acquired at any time | |||||||||
| (3) | Lock are acquired in the first phase | |||||||||
| (4) | None of the above | |||||||||
| Correct Answer: Lock are acquired in the first phase | ||||||||||
| Q 45: | Which of the following is not a file operation? | |||||||||
| (1) | Find | |||||||||
| (2) | Find Next | |||||||||
| (3) | Reset | |||||||||
| (4) | None of the above | |||||||||
| Correct Answer: Reset | ||||||||||
| Q 46: | If, instead of Nested-loop join, Block nested-loop join is used, again with the most appropriate choice of table in the outer loop, the reduction in number of block accesses required for reading the data will be | |||||||||
| (1) | 38400 | |||||||||
| (2) | 30400 | |||||||||
| (3) | 0 | |||||||||
| (4) | 798400 | |||||||||
| Correct Answer: 38400 | ||||||||||
| Q 47: | Relation produced from an E-R model will always be in | |||||||||
| (1) | First normal form | |||||||||
| (2) | Second normal form | |||||||||
| (3) | Third normal form | |||||||||
| (4) | Fourth normal form | |||||||||
| Correct Answer: First normal form | ||||||||||
| Q 48: | Which of the following is NOT a part of the ACID properties of database transactions? | |||||||||
| (1) | Isolation | |||||||||
| (2) | Consistency | |||||||||
| (3) | Atomicity | |||||||||
| (4) | Deadlock-Freedom | |||||||||
| Correct Answer: Deadlock-Freedom | ||||||||||
| Q 49: | The DUAL table has | |||||||||
| (1) | Many tows and many columns | |||||||||
| (2) | One column with many rows | |||||||||
| (3) | One row and one column | |||||||||
| (4) | One row with many columns | |||||||||
| Correct Answer: One row and one column | ||||||||||
| Q 50: | Which is the best suitable for sequential access of data? | |||||||||
| (1) | B+ tree | |||||||||
| (2) | B tree | |||||||||
| (3) | Both (a) and (b) | |||||||||
| (4) | None of the above | |||||||||
| Correct Answer: Both (a) and (b) | ||||||||||
| Q 51: | Which of the following group functions ignore NULL values? | |||||||||
| (1) | MAX | |||||||||
| (2) | SUM | |||||||||
| (3) | COUNT | |||||||||
| (4) | All of these | |||||||||
| Correct Answer: All of these | ||||||||||
| Q 52: | Which of the following SQL commands can be used to modify existing data in a database table? | |||||||||
| (1) | MODIFY | |||||||||
| (2) | UPDATE | |||||||||
| (3) | NEW | |||||||||
| (4) | CHANGE | |||||||||
| Correct Answer: UPDATE | ||||||||||
| Q 53: | Which of these are true of Collection types? | |||||||||
| (1) | They store data of the same data type | |||||||||
| (2) | They are unconstrained | |||||||||
| (3) | They are sparse | |||||||||
| (4) | All of these | |||||||||
| Correct Answer: All of these | ||||||||||
| Q 54: | Which of the following SQL commands can be used to add data to a database table? | |||||||||
| (1) | UPDATE | |||||||||
| (2) | APPEND | |||||||||
| (3) | ADD | |||||||||
| (4) | INSERT | |||||||||
| Correct Answer: INSERT | ||||||||||
| Q 55: | Which of the following is dense index? | |||||||||
| (1) | Primary index | |||||||||
| (2) | Clusters index | |||||||||
| (3) | Secondary index | |||||||||
| (4) | Secondary non key index | |||||||||
| Correct Answer: Secondary index | ||||||||||
| Q 56: | In RDBMS, which type of join returns all rows that satisfy the join condition? | |||||||||
| (1) | Inner Join | |||||||||
| (2) | Outer Join | |||||||||
| (3) | Semi Join | |||||||||
| (4) | Anti Join | |||||||||
| Correct Answer: Inner Join | ||||||||||
| Q 57: | Which protocol is not used for electronic mail? | |||||||||
| (1) | SMTP | |||||||||
| (2) | MIME | |||||||||
| (3) | IMAP | |||||||||
| (4) | SNMP | |||||||||
| Correct Answer: SNMP | ||||||||||
| Q 58: | Cell Relay, also known as | |||||||||
| (1) | ISDN | |||||||||
| (2) | X.25 | |||||||||
| (3) | ATM | |||||||||
| (4) | Frame Relay | |||||||||
| Correct Answer: ATM | ||||||||||
| Q 59: | Baud is : | |||||||||
| (1) | Number of bits transmitted per unit time | |||||||||
| (2) | Number of bytes transmitted per unit time | |||||||||
| (3) | Number of signal changes per second | |||||||||
| (4) | None of these | |||||||||
| Correct Answer: Number of signal changes per second | ||||||||||
| Q 60: | DNS Client is also knows as: | |||||||||
| (1) | DNS updates | |||||||||
| (2) | DNS resolver | |||||||||
| (3) | DNS handler | |||||||||
| (4) | None of these | |||||||||
| Correct Answer: DNS resolver | ||||||||||
| Q 61: | Identify the class of IPv4 address 191.1.2.3 | |||||||||
| (1) | Class A | |||||||||
| (2) | Class B | |||||||||
| (3) | Class C | |||||||||
| (4) | Class D | |||||||||
| Correct Answer: Class B | ||||||||||
| Q 62: | A television broadcast is an example of __________ transmission. | |||||||||
| (1) | Half-duplex | |||||||||
| (2) | Full-duplex | |||||||||
| (3) | Simplex | |||||||||
| (4) | Automatic | |||||||||
| Correct Answer: Simplex | ||||||||||
| Q 63: | In a Go-Back-N ARQ, if the window size is 63, what is the range of sequence numbers? | |||||||||
| (1) | 0 to 63 | |||||||||
| (2) | 1 to 63 | |||||||||
| (3) | 0 to 64 | |||||||||
| (4) | 1 to 64 | |||||||||
| Correct Answer: 0 to 63 | ||||||||||
| Q 64: | The process that dynamically assigns an IP address to a network device is called? | |||||||||
| (1) | DNS | |||||||||
| (2) | DHCP | |||||||||
| (3) | NAT | |||||||||
| (4) | MAC | |||||||||
| Correct Answer: DHCP | ||||||||||
| Q 65: | In Point-to-point Protocol (PPP), network layer option are negotiated using | |||||||||
| (1) | Link Control Protocol | |||||||||
| (2) | Dynamic Host Control Protocol | |||||||||
| (3) | Internet Protocol | |||||||||
| (4) | Network Control Protocol | |||||||||
| Correct Answer: Network Control Protocol | ||||||||||
| Q 66: | Which of the following is the character oriented protocol | |||||||||
| (1) | SDLC | |||||||||
| (2) | HDLC | |||||||||
| (3) | BiSYNC | |||||||||
| (4) | LAPB | |||||||||
| Correct Answer: BiSYNC | ||||||||||
| Q 67: | An ATM cell is ................ bytes long. | |||||||||
| (1) | 53 | |||||||||
| (2) | 5 | |||||||||
| (3) | 48 | |||||||||
| (4) | 60 | |||||||||
| Correct Answer: 53 | ||||||||||
| Q 68: | Dirty bit is used to show the | |||||||||
| (1) | Page with corrupted data | |||||||||
| (2) | The wrong page in the memory | |||||||||
| (3) | Page that is modified after being loaded into a cache memory | |||||||||
| (4) | Page that is less frequently accessed | |||||||||
| Correct Answer: Page that is modified after being loaded into a cache memory | ||||||||||
| Q 69: | For a parallel projection the center of projection is always at ............... which makes the projection parallel. | |||||||||
| (1) | Infinity | |||||||||
| (2) | Origin | |||||||||
| (3) | Center | |||||||||
| (4) | None of these | |||||||||
| Correct Answer: Infinity | ||||||||||
| Q 70: | What is the Standard HTTP port? | |||||||||
| (1) | 80 | |||||||||
| (2) | 161 | |||||||||
| (3) | 21 | |||||||||
| (4) | 1024 | |||||||||
| Correct Answer: 80 | ||||||||||
| Q 71: | Suppose computers A and B have IP addresses 10.105.1.113 and 10.105.1.91 respectively and they both use the same netmask N. Which of the values of N given below should not be used if A and B should belong to the same network? | |||||||||
| (1) | 255.255.255.0 | |||||||||
| (2) | 255.255.255.128 | |||||||||
| (3) | 255.255.255.192 | |||||||||
| (4) | 255.255.255.224 | |||||||||
| Correct Answer: 255.255.255.224 | ||||||||||
| Q 72: | Packets of the same session may be routed through different paths in | |||||||||
| (1) | TCP, but not UDP | |||||||||
| (2) | TCP and UDP | |||||||||
| (3) | UDP, but not TCP | |||||||||
| (4) | Neither TCP, not UDP | |||||||||
| Correct Answer: TCP and UDP | ||||||||||
| Q 73: | A packet whose destination is outside the local TCP/IP network segment is sent to .......... | |||||||||
| (1) | File server | |||||||||
| (2) | DNS server | |||||||||
| (3) | DHCP server | |||||||||
| (4) | Default gateway | |||||||||
| Correct Answer: DNS server | ||||||||||
| Q 74: | A slotted ALOHA network transmits 200-bits frames using a shared channel with a 200 Kbps bandwidth. Find the throughput of the system, if the system (all stations put together) produces 250 frames per second : | |||||||||
| (1) | 49 | |||||||||
| (2) | 368 | |||||||||
| (3) | 149 | |||||||||
| (4) | 46 | |||||||||
| Correct Answer: 46 | ||||||||||
| Q 75: | When data is encapsulated, which is the correct order? | |||||||||
| (1) | Data, frame, packet, segment, bit | |||||||||
| (2) | Segment, data, packet, frame, bit | |||||||||
| (3) | Data, segment, packet, frame, bit | |||||||||
| (4) | Data, segment frame, packet, bit | |||||||||
| Correct Answer: Data, segment, packet, frame, bit | ||||||||||
| Q 76: | How many non-overlapping channels are available with 802.11g? | |||||||||
| (1) | 3 | |||||||||
| (2) | 12 | |||||||||
| (3) | 18 | |||||||||
| (4) | 42 | |||||||||
| Correct Answer: 3 | ||||||||||
| Q 77: | The network address of 172.16.0.0/19 provides how many subnets and hosts? | |||||||||
| (1) | 7 subnets, 30 hosts each | |||||||||
| (2) | 8 subnets, 8190 hosts each | |||||||||
| (3) | 8 subnets, 2046 hosts each | |||||||||
| (4) | 7 subnets, 2046 hosts each | |||||||||
| Correct Answer: 8 subnets, 8190 hosts each | ||||||||||
| Q 78: | What is the maximum distance running the lowest data rate for 802.11g? | |||||||||
| (1) | About 100 feet | |||||||||
| (2) | About 175 feet | |||||||||
| (3) | About 300 feet | |||||||||
| (4) | About 400 feet | |||||||||
| Correct Answer: About 300 feet | ||||||||||
| Q 79: | You want to ping the loopback address of your local host. What will you type? | |||||||||
| (1) | ping 127.0.0.1 | |||||||||
| (2) | ping 0.0.0.0 | |||||||||
| (3) | ping :: 1 | |||||||||
| (4) | trace 0.0.:.1 | |||||||||
| Correct Answer: ping :: 1 | ||||||||||
| Q 80: | The OSI model has .................. layers. | |||||||||
| (1) | 4 | |||||||||
| (2) | 7 | |||||||||
| (3) | 6 | |||||||||
| (4) | 5 | |||||||||
| Correct Answer: 7 | ||||||||||
| Q 81: | Find the missing number in the following series: | |||||||||
| (1) | 9 | |||||||||
| (2) | 10 | |||||||||
| (3) | 11 | |||||||||
| (4) | 12 | |||||||||
| Correct Answer: 10 | ||||||||||
| Q 82: | Which number should be in the square marked by the question mark?
| |||||||||
| (1) | 2 | |||||||||
| (2) | 3 | |||||||||
| (3) | 5 | |||||||||
| (4) | 16 | |||||||||
| Correct Answer: 2 | ||||||||||
| Q 83: | Find the missing number marked by the question mark: | |||||||||
| (1) | 12 | |||||||||
| (2) | 13 | |||||||||
| (3) | 11 | |||||||||
| (4) | 15 | |||||||||
| Correct Answer: 12 | ||||||||||
| Q 84: | The clock in my lounge room is 10 minutes slower than the clock on my phone, which is 6 minutes slow. My tram always leaves 6 minutes early, although it is scheduled for 8:55am. It takes me 20 minutes to get to the tram stop. What time must I leave, according to my lounge room clock, in order to catch my tram? | |||||||||
| (1) | 8:49am | |||||||||
| (2) | 8:35am | |||||||||
| (3) | 8:23am | |||||||||
| (4) | 8:13am | |||||||||
| Correct Answer: 8:13am | ||||||||||
| Q 85: | Choose a box that is not different to the box formed from the given sheet of paper (X).
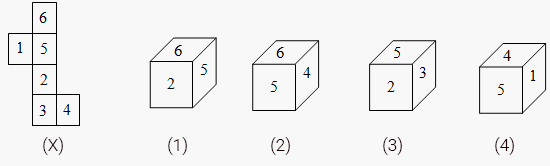 | |||||||||
| (1) | 1 | |||||||||
| (2) | 2 | |||||||||
| (3) | 3 | |||||||||
| (4) | 4 | |||||||||
| Correct Answer: 2 | ||||||||||
| Q 86: | Which symbol will be on the face opposite to the face with symbol ‘C’ ?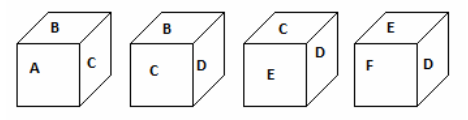 | |||||||||
| (1) | A | |||||||||
| (2) | B | |||||||||
| (3) | E | |||||||||
| (4) | F | |||||||||
| Correct Answer: F | ||||||||||
| Q 87: | From the positions of a cube are shown below, Which letter will be on the face opposite to face with '1'?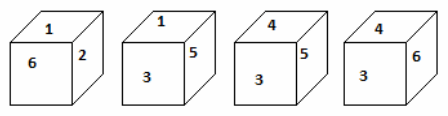 | |||||||||
| (1) | 5 | |||||||||
| (2) | 6 | |||||||||
| (3) | 3 | |||||||||
| (4) | 4 | |||||||||
| Correct Answer: 4 | ||||||||||
| Q 88: | Look at this series: 2, 1, (1/2), (1/4), ... What number should come next? | |||||||||
| (1) | 1/5 | |||||||||
| (2) | 1/6 | |||||||||
| (3) | 1/7 | |||||||||
| (4) | 1/8 | |||||||||
| Correct Answer: 1/8 | ||||||||||
| Q 89: | Look at this series: 7, 10, 8, 11, 9, 12, ... What number should come next? | |||||||||
| (1) | 7 | |||||||||
| (2) | 10 | |||||||||
| (3) | 12 | |||||||||
| (4) | 13 | |||||||||
| Correct Answer: 10 | ||||||||||
| Q 90: | Look at this series: 53, 53, 40, 40, 27, 27, ... What number should come next? | |||||||||
| (1) | 12 | |||||||||
| (2) | 14 | |||||||||
| (3) | 27 | |||||||||
| (4) | 53 | |||||||||
| Correct Answer: 14 | ||||||||||
| Q 91: | राजस्थान राज्य के कुल क्षेत्रफल तथा कुल जनसँख्या को कौन सा जिला लगभग एक सामान प्रतिशत अंश रखता है | |||||||||
| (1) | बांसवाडा | |||||||||
| (2) | चुरू | |||||||||
| (3) | सीकर | |||||||||
| (4) | सिरोही | |||||||||
| Correct Answer: सिरोही | ||||||||||
| Q 92: | राजस्थान के किस जिले की सीमा अंतर्राज्यीय व अंतर्राष्ट्रीय दोनों है | |||||||||
| (1) | जैसलमेर | |||||||||
| (2) | गंगानगर | |||||||||
| (3) | बीकानेर | |||||||||
| (4) | झालावाड | |||||||||
| Correct Answer: गंगानगर | ||||||||||
| Q 93: | निम्न में से किस जिले की सीमा पाकिस्तान से नहीं लगती - | |||||||||
| (1) | बाड़मेर | |||||||||
| (2) | बीकानेर | |||||||||
| (3) | गंगानगर | |||||||||
| (4) | हनुमानगढ़ | |||||||||
| Correct Answer: हनुमानगढ़ | ||||||||||
| Q 94: | वह जिला जिसकी सीमा पाकिस्तान एवं गुजरात दोनों से लगती है | |||||||||
| (1) | बाड़मेर | |||||||||
| (2) | जालौर | |||||||||
| (3) | जैसलमेर | |||||||||
| (4) | सिरोही | |||||||||
| Correct Answer: बाड़मेर | ||||||||||
| Q 95: | बाड़मेर जिले की सीमा किससे नहीं मिलती है ? | |||||||||
| (1) | सांचोर | |||||||||
| (2) | सिरोही | |||||||||
| (3) | जोधपुर | |||||||||
| (4) | जैसलमेर | |||||||||
| Correct Answer: सिरोही | ||||||||||
| Q 96: | निम्न में से कोनसा राजस्थान का शहर पाकिस्तान सीमा के निकट है ? | |||||||||
| (1) | बीकानेर | |||||||||
| (2) | जैसलमेर | |||||||||
| (3) | गंगानगर | |||||||||
| (4) | हनुमानगढ़ | |||||||||
| Correct Answer: गंगानगर | ||||||||||
| Q 97: | सिन्धु घाटी से अलग एक हड़प्पा उत्खननकर्ताओ द्वारा निम्नलिखित में से किसका वर्णन किया गया है - | |||||||||
| (1) | कुरदा | |||||||||
| (2) | वेनारा | |||||||||
| (3) | कालीबंगा | |||||||||
| (4) | बिहारीपुरा | |||||||||
| Correct Answer: कालीबंगा | ||||||||||
| Q 98: | वन्दे मातरम् योजना किसके द्वारा संचालित की जा रही है - | |||||||||
| (1) | सामाजिक अधिकारिता मंत्रालय द्वारा | |||||||||
| (2) | चिकित्सा मंत्रालय द्वारा | |||||||||
| (3) | गृह मंत्रालय द्वारा | |||||||||
| (4) | शिक्षा मंत्रालय द्वारा | |||||||||
| Correct Answer: चिकित्सा मंत्रालय द्वारा | ||||||||||
| Q 99: | निम्न में से किस योजना का उद्देश्य लंबित राजस्व अदालती मामलो को निपटाना है | |||||||||
| (1) | सरकार आपके द्वार | |||||||||
| (2) | प्रशासन आपके द्वार | |||||||||
| (3) | न्याय आपके द्वार | |||||||||
| (4) | पुलिस आपके द्वार | |||||||||
| Correct Answer: न्याय आपके द्वार | ||||||||||
| Q 100: | राष्ट्रिय मरू उद्यान को किस नाम से भी जाना जाता है ? | |||||||||
| (1) | वनस्पति पार्क | |||||||||
| (2) | वन्य जिव उद्यान | |||||||||
| (3) | घास-क्षेत्र पार्क | |||||||||
| (4) | जीवाश्म पार्क | |||||||||
| Correct Answer: जीवाश्म पार्क | ||||||||||